CRC Definition
Data exchange in the modern digital environment occurs at an incredible pace and passes through various communication channels and storage systems. Just imagine how difficult it is to ensure the integrity of information with such a set of requirements.
Overall, CRC (Cyclic Redundancy Check) is currently considered an expert among technologies that allow detecting errors in computer networks, data storage systems, telecommunications, and other areas of information technology.
In essence, this is a cyclic redundancy check, which fully corresponds to the basic principle of the algorithm. Algorithmic codes work in continuous cycles, constantly checking whether any unplanned or unauthorized changes occur in the transmitted information.
We can say that the basis of CRC is that it constantly adds a set number of check bits to the transmitted message, which works as a detector or analyzer of possible inaccuracies or discrepancies. To better understand what a check bit is, take an 8-bit data block as a basis, although it should be remembered that their size may differ in each individual situation.
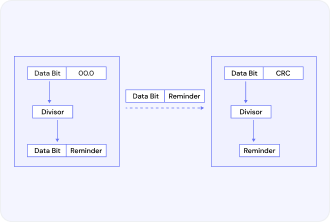
Working principles and mathematical foundations of CRC
Generally, CRC operates on the basis of a mathematical model, which is based on operations carried out on polynomials in the Galois field GF(2), within which all coefficients can only take the values 0 or 1. All calculations go through certain stages, including the selection of a generating polynomial, adding zeros, polynomial division, obtaining a remainder, and forming the final message.
During the verification and checking of data integrity, similar operations are performed:
- receiving a message, evaluating the CRC sum, and analyzing it,
- repeated calculation, within which the CRC of the data is created,
- comparison of the calculation results and the obtained CRC sum, and if they are identical, the data is intact,
- indication of an error in case of a discrepancy in the sums.
As a matter of fact, such a comprehensive and well-established approach allows you to avoid any inaccuracy, and cyclical and constant verification of results excludes even minimal errors. That is why any employee of the outsource software development company in the UK will unconditionally confirm the value of CRC.
CRC types and standards
To cover the needs of various applications and optimize operations for their needs, there are several types of standardized CRCs, the data on which are given in the table below:
| CRC type | Size (bits) | Field of application |
| CRC-8 | 8 | Embedded systems, sensors |
| CRC-16 | 16 | Modem protocols, USB |
| CRC-32 | 32 | Ethernet, ZIP archives |
| CRC-64 | 64 | Highly reliable systems |
Additionally, there are also specialized implementations for different industries, for example:
- CRC-CCITT used for telecommunication protocols,
- CRC-ANSI is commonly applied in industrial networks,
- CRC-IEEE is a standard for Ethernet network protocols,
- CRC-ITU meets international protocols for telecommunications.
As can be seen from the above, this is a kind of universal tool, ready for modification to the necessary parameters. This means that it is able to solve any problems, both in web design agencies in Australia and any other similar organizations, without giving errors and inaccuracies a single chance.
Practical application and advantages
It is difficult to assess the value of CRC based solely on theory, because practical application reveals all facets of this tool, allowing you to see how the approach is implemented in each individual technological solution.
You can talk for a long time about the advantages of CRC, but its versatility has allowed it to take a strong position in almost all areas of the modern digital industry. From the simplest embedded devices to complex corporate systems — everywhere it is necessary to track and identify errors, and this assistant copes with this task 100%!
Application areas
Let’s take a closer look at the range of CRC applications to understand how different users can implement its capabilities with maximum efficiency, as the needs of a UX design agency in London focused on user experience and a SaaS development company will differ greatly.
- Computer networks — verify data packet integrity in Ethernet, Wi-Fi, and TCP/IP networks.
- Storage programs — tools to identify read/write errors in hard drives, SSDs, and optical media.
- File systems — ensure metadata integrity for most modern file systems.
- Data transfer protocols — CRC checks are used in serial interfaces, USB, SATA, and others.
- Embedded platforms — check the firmware and quality of configuration data in microcontrollers and IoT devices.
On account of this, each of these areas has its own specific requirements for the speed of request processing, the size of checksums, and the level of security, which once again speaks of the high adaptability of CRC and the ability to be modified for different operating conditions.
Main advantages of the technology
As we learn more and more about CRC, we can highlight the key factors that have played a significant role in establishing it as a de facto standard in many cases. In addition to adaptability and versatility, we also note the following important features:
- excellent detection efficiency, which allows CRC to identify almost all single and double errors,
- low computational costs, since the algorithm is easily implemented in both software and hardware,
- determinism, which guarantees a certain result for any specific data sets,
- scalability, which makes it possible to change the configuration for different data sizes and reliability requirements,
- standardization according to international standards and ensuring compatibility between different systems.
Therefore, the incredible effect obtained from the synergy of these advantages allows CRC to remain relevant even when new tools and cryptographic methods of integrity control appear on the scene every day.
Conclusion
After such a detailed analysis, it is easy to conclude that Cyclic Redundancy Check is currently one of the frontliners on the data integrity stage. Adapting to rapidly changing conditions, it confidently holds a leading position in the modern information structure.
And despite the fact that this is not exactly a method for correcting errors, but just a way to detect them, its importance should not be underestimated, since it has no competitors in modern data transmission and storage systems yet.